Computer science researchers introduce Telex to circumvent state-level internet censorship
 Enlarge
Enlarge
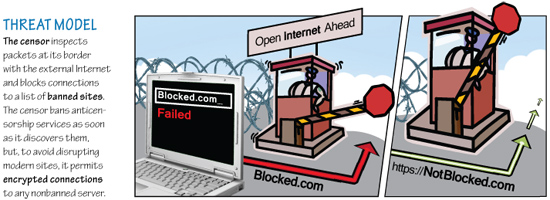
Researchers at the University of Michigan and the University of Waterloo in Canada have developed Telex, a new approach to circumventing Internet censorship that is intended to help the citizens of repressive governments to freely access online services and information. Telex would place anticensorship technology into the Internet’s core network infrastructure, essentially turning the whole web into a proxy server and making it far more difficult than today for a censoring government to block individual sites.
The researchers, led by Assistant Professor J. Alex Halderman, include PhD students Eric Wustrow and Scott Wolchok, and Associate Professor Ian Goldberg at the University of Waterloo. They have documented their findings in the paper, “Telex: Anticensorship in the Network Infrastructure,” which Mr. Wustrow presented on Aug. 12 at the 20th USENIX Security Symposium in San Francisco.
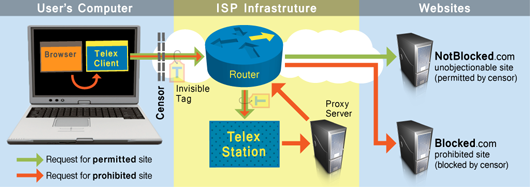
Telex is markedly different from past anticensorship systems, is easy to distribute, and is very difficult to detect and block. The Telex concept is to place anticensorship technology into the Internet’s core network infrastructure through cooperation from large Internet Service Providers (ISPs), who would deploy Telex stations on paths between censors’ networks and popular, uncensored Internet destinations. Telex leverages censors’ unwillingness to completely block day-to-day Internet access and secretly converts innocuous, unblocked websites into proxies. Users within the repressive regime would need to obtain and install Telex client software onto their computers.
When a Telex user wants to visit a blacklisted site, the client software establishes an encrypted HTTPS connection to a non-blacklisted web server outside the censor’s network, which could be a normal site that the user regularly visits. Since the connection looks normal, the censor allows it, but this connection is only a decoy.
The Telex client software secretly marks the connection as a Telex request by inserting a cryptographic tag into the headers, using a mechanism called public-key steganography. This means anyone can tag a connection using only publicly available information, but only the Telex service (using a private key) can recognize that a connection has been tagged. User requests with tags will be recognized by Telex stations as connections from Telex clients and that traffic would be would transparently diverted to the forbidden website or service instead.
 Enlarge
Enlarge
The researchers have demonstrated the system by creating one Telex station on a mock ISP in their lab at the University of Michigan. Though the system is still a research prototype, it has been accessed by a steadily increasing number of users from around the world, including users in countries that heavily censor the Internet.
Professor Halderman’s research spans applied computer security and tech-centric public policy. His interests include software security, data privacy, electronic voting, anticensorship, digital rights management, and cybercrime, as well as technological aspects of intellectual property law and government regulation. He teaches Introduction to Computer Security (EECS 398) and Computer and Network Security (EECS 588).
Prof. Halderman’s recent research projects have included exposing security weaknesses in Washington DC’s Internet-based absentee voting system and in India’s electronic voting machines.
More Information
 MENU
MENU 
